(And the SHA256 Hash That Did It)
You ever have one of those days where your emails vanish like a magician’s assistant, no bounce-back, no error, just poof into Defender’s shadow realm?
Yeah. That was me last week.
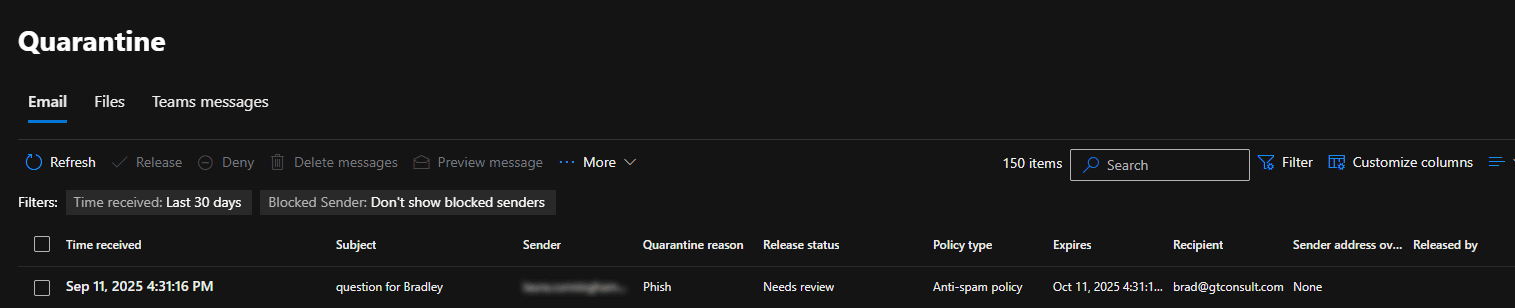
Internal users were sharing files via SharePoint, or receiving Planner tasks, or even just sending standard Outlook attachments — and bam, straight into quarantine. These were clean emails. Trusted senders. Internal communication. Not a hint of malware. Yet Microsoft Defender decided they were guilty until proven... SHA256.
Let’s unpack this.
The Mystery: When Even Internal Emails Get Slammed by Defender
Everything looked legit:
- SPF, DKIM, DMARC all green
- TNEF disabled to avoid winmail.dat issues
- Mail flow rules in place with SCL -1
- Users added to the Tenant Allow List
- SharePoint-generated messages?

Still, these emails were being quarantined with the dreaded reason:
"Blocked by organization policy: Tenant Allow/Block List attachment blocked"
Naturally, I went full gorilla mode.
The Red Herrings: TNEF, Preset Policies, and Mail Flow Rules
I did what any email admin would do. I:
Nothing.
Still quarantined. Still Defender screaming “BLOCKED!” like a bouncer at a VIP-only nightclub.
The Twist: A “Files” Entry in the Tenant Allow/Block List
Then I looked somewhere I hadn’t checked in a while:
Microsoft 365 Defender > Policies & Rules > Tenant Allow/Block List > Files
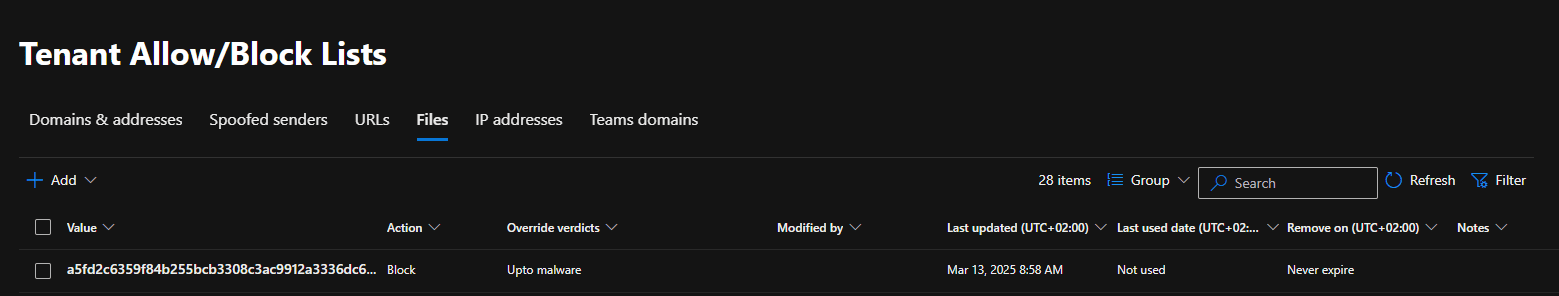
And there it was:
A blocked file hash. A SHA256 fingerprint sitting there silently ruining lives.
The hash matched a file that users were sharing via SharePoint. Meaning: any email containing that specific file — even internal — was nuked.
No error. No alert. Just gone.
This is the Defender equivalent of:

"I didn’t block your email. I blocked your vibe. And that file’s vibe was off."

The Fix: Yank the Hash, Free the Mail
Lessons Learned (So You Don’t Suffer Like I Did)
Allow/Block List
Always check the Files tab in the Allow/Block List — not just Senders and Domains.
File Hash Blocking
Defender does not care if a file is internal or externally shared — if its hash is blocked, it's toast.
Preset Policy Limitations
Preset security policies are powerful, but they don’t honor Allow entries for internal senders with blocked file hashes.
Sender Identity vs. Trust
Just because the sender is "you" doesn't mean Defender trusts you — especially when SharePoint wraps your message in a system-generated hug and sends it with a blocked attachment.
Final Thoughts

Barend Olivier is the Support Manager at GTconsult, managing a team that keeps Microsoft 365, SharePoint, and cloud environments secure and running smoothly. He started his career in telecommunications, explored the SOC space, and found his home in the Microsoft world. Growing up surrounded by computers and non stop gaming, he developed a love for building and fixing them and today, he continues to believe that technology is one of the best tools we have for making life more manageable in an ever-changing world.
