Watch Out: Think before you click
Phishing attacks have become increasingly deceptive— if you're not careful, it's easy to fall for one. Some prey on our tendency to skim emails, rely on visual cues like familiar logos or jargon, or respond hastily to anything marked as urgent. They’re not always complex— many are simple, but just convincing enough to earn your trust if you’re not paying attention.

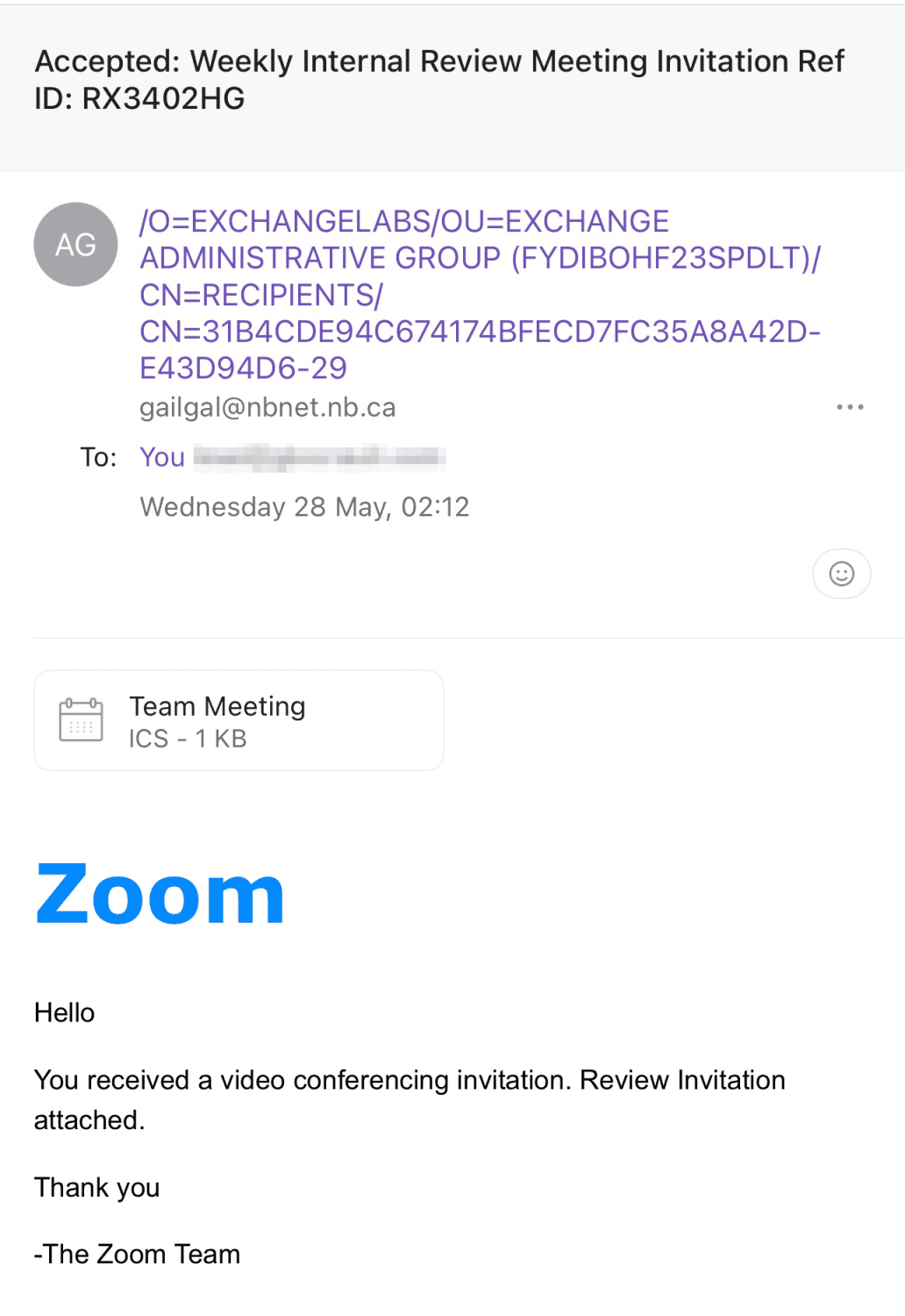
Received something like this before?
- "Your Zoom account is suspended"
- "You missed a Zoom meeting"
- "New Zoom message received"
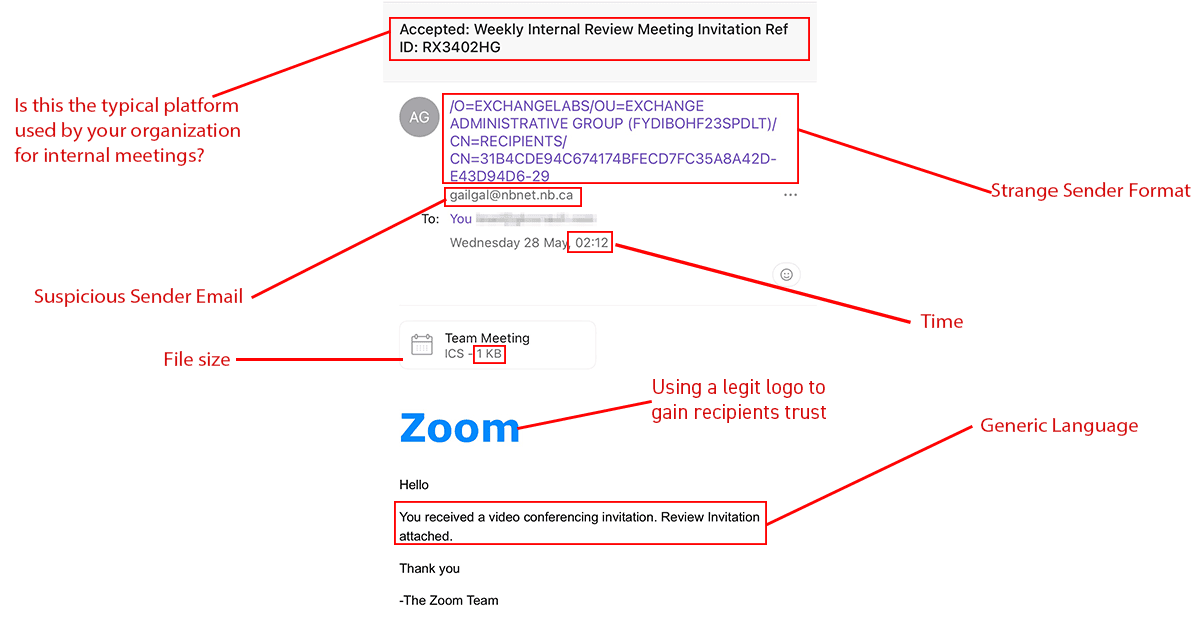
Platform
While this may not apply to all organizations, it's still something to consider. If your organization holds all internal meetings on a different platform (such as Teams). Receiving an email inviting you to a weekly meeting on Zoom might be an immediate red flag. Also, if you notice, it says 'accepted'- be careful not to click the link to find out what exactly you accepted.
Strange sender format

The use of a legit logo to gain trust
When you first click open the email, the first thing that draws your attention is the Zoom logo. It's familiar/recognizable, so if you're skimming through, you may let your guard down and miss all the other red flags.
Suspicious sender email

Generic language

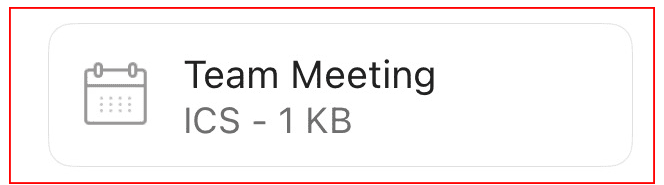
File size
Odd Time

Other red flags to look out for
The takeaway?
- Who sent it?
- What are they asking?
- Does this align with how your organization usually communicates?
Want to check if your MS365 Environment is prepared for the just in case?
We recommend getting a penetration test to ensure your organization is well-protected against potential vulnerabilities and attacks. A thorough assessment can uncover weaknesses before cybercriminals do, giving you the opportunity to strengthen your defences and train your team. Don't wait for a breach to take action!
