You know your Secure Score should be higher. You've read about configuration drift eating away at your security posture. You understand that lack of capacity is keeping your score stuck.

This is the trap most IT teams fall into: they start implementing recommendations in order of points or ease, without understanding which changes actually matter for their specific risk profile—or how to sustain improvements once they're made.
The result? Wasted effort on low-impact changes, broken workflows from poorly planned implementations, and scores that plateau or even decline despite your best efforts.
Why Most Secure Score Improvement Efforts Fail
The typical approach looks something like this: open the Microsoft Defender portal, see a list of recommendations, pick the ones worth the most points or that seem easiest, and start implementing.
Three months later, your score has barely moved. Or it moved briefly and then dropped back down. Or you've spent weeks on improvements that broke critical workflows and had to be rolled back.
The problem isn't lack of effort. It's lack of strategy.
Effective Secure Score improvement requires understanding three things most teams skip:
The Hidden Complexity of "Simple" Recommendations

Let's take what seems like a straightforward recommendation: enable MFA for all users.
Sounds simple, right? But actually implementing it requires understanding:
- Which users already have MFA and which don't
- Whether you have Conditional Access policies that conflict
- Which applications might break with MFA enforcement
- How to handle service accounts and automated processes
- What exceptions might be legitimately needed
- How to communicate changes to users effectively
Get any of these wrong and you'll spend more time fixing problems than you saved by implementing the recommendation.
This pattern repeats across every recommendation in your Secure Score. What looks like a configuration change on the surface requires strategic thinking about business impact, technical dependencies, and change management.
Why Quick Wins Aren't Always Quick
IT teams often start with "quick wins"—recommendations that promise high point values with supposedly minimal effort.
The problem is that "quick" depends entirely on your environment's current state and complexity. Blocking legacy authentication might take 15 minutes in one organization and require weeks of application modernization in another.
More importantly, chasing points without understanding impact leads to a dangerous pattern: implementing changes that raise your score but don't actually improve your security posture in meaningful ways for your specific risk profile.
The organizations that successfully improve their Secure Score don't focus on quick wins first. They focus on right wins—improvements that align with their actual threat landscape and business priorities, regardless of point value.
The Sustainability Problem
Here's what happens in most organizations: someone dedicates focused time to Secure Score improvements. Over a few weeks or months, the score increases. Victory!
Six months later, the score has drifted back down. Temporary exceptions became permanent. New users onboarded without inheriting security policies. Applications deployed without security review.
The improvements weren't sustained because they weren't integrated into operational processes. Security became a project with an end date, not an ongoing practice.
Sustainable Secure Score improvement requires building security into your regular workflows:
- User onboarding processes that automatically apply security policies
- Regular reviews of exceptions and elevated access
- Monitoring that flags when configurations drift from baseline
- Documentation that survives staff turnover
Without these processes, you're constantly fighting to maintain improvements instead of compounding them over time.
What Actually Works
Organizations that successfully improve and maintain their Secure Score approach it systematically:
They understand their current state before implementing anything. Where are the critical gaps? Which recommendations address real risks versus checking compliance boxes? What's the business impact of each change?
They prioritize strategically, not by points. High-impact security improvements for their specific environment come first, even if they're worth fewer points than easier changes.
They test before deploying widely. Pilot changes with a small group. Identify and address issues. Then expand systematically with proper change management.
They build monitoring into operations. Regular review processes catch drift before it becomes significant. Documentation ensures knowledge doesn't live in one person's head.
They know when to get help. Some improvements require specialized expertise most internal teams don't have time to develop. Recognizing this early prevents wasted effort on approaches that won't work.
The Path Forward Depends on Your Situation
Some organizations can improve their Secure Score significantly with internal resources—if they have the right strategic approach and dedicate consistent effort over time.
Others reach a plateau where further improvement requires either:
- Specialized Microsoft 365 security expertise their team hasn't developed
- Time investment their team genuinely doesn't have capacity for
- Licensing and tools their current budget doesn't include
Neither scenario is wrong. The question is whether you're willing to accept your current risk level or invest in further improvement.
But regardless of which path you choose, attempting Secure Score improvement without a systematic approach leads to wasted effort, broken workflows, and minimal sustained progress.
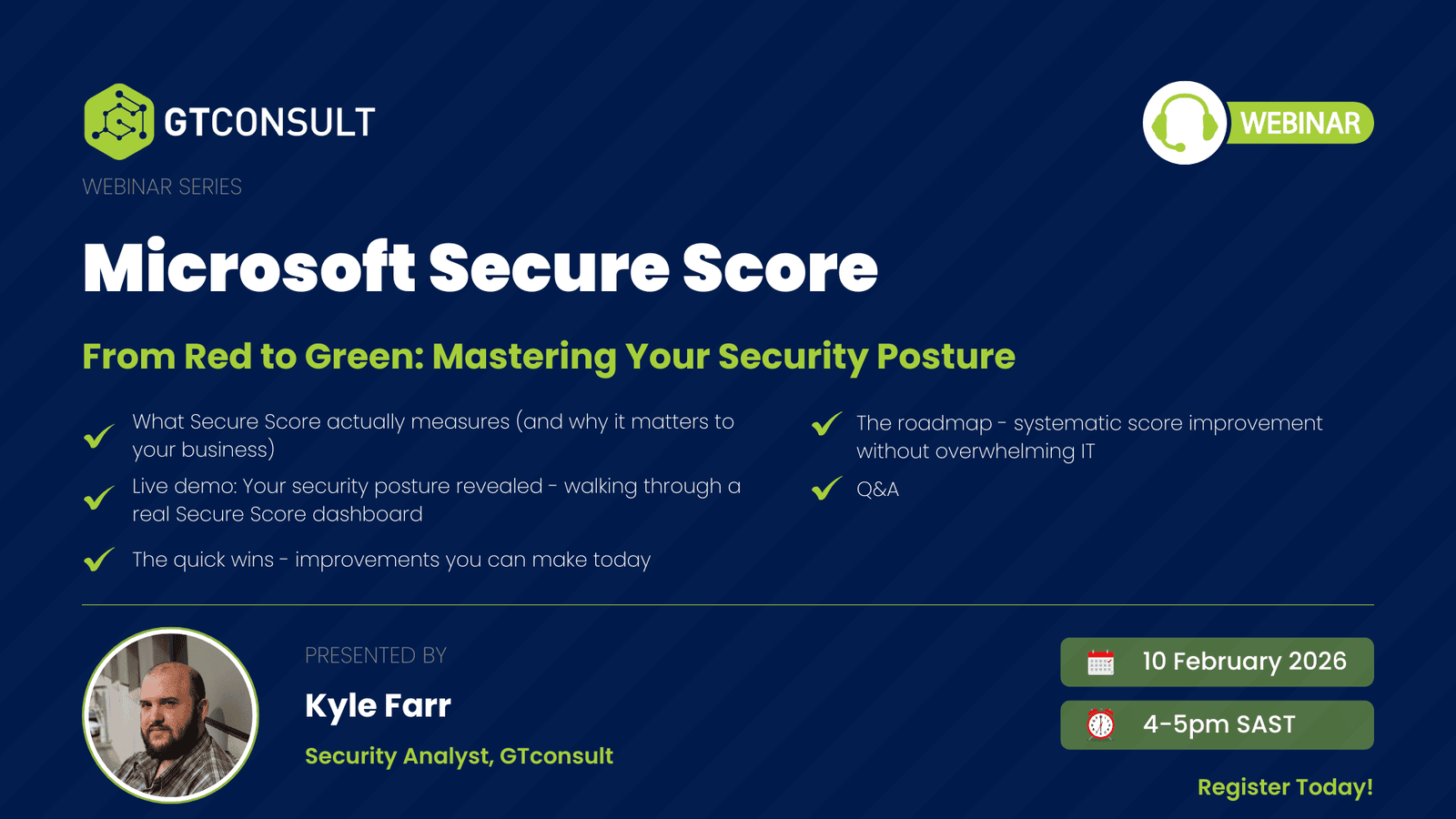
See the Strategic Approach In Action
Understanding why most Secure Score improvement efforts fail is one thing. Knowing how to avoid those pitfalls and implement changes that actually stick is another.
Join our security analyst, Kyle Farr, on 10th of February 2026 for a live demonstration of strategic Secure Score improvement:
- Current state analysis - How to assess your score breakdown and identify what actually matters for your risk profile (not just point values)
- Prioritization framework - The decision criteria for determining which recommendations to tackle first based on business impact and technical dependencies
- Live implementation walkthrough - Watch a real security control get configured with proper testing and rollback planning
- Monitoring and sustainability - Building the processes that catch drift before it degrades your security posture
- Q&A for your specific challenges - Get answers about your environment's blockers and constraints
This isn't theory or generic advice. It's a practical demonstration of the systematic approach that separates successful Secure Score improvement from wasted effort.
📅 February 10, 2026 | 4:00 PM - 5:00 PM SAST
If you've been stuck between understanding your security gaps and actually addressing them effectively, this is the bridge you need.
