
GTconsult A Team Protection
We hack you before you get hacked. Hire a hacker and receive a real-world attack scenario without the devastating consequences. Mitigate your risk with the cover of A Team Protection.
Mitigate your risks.
External Penetration Assessment.
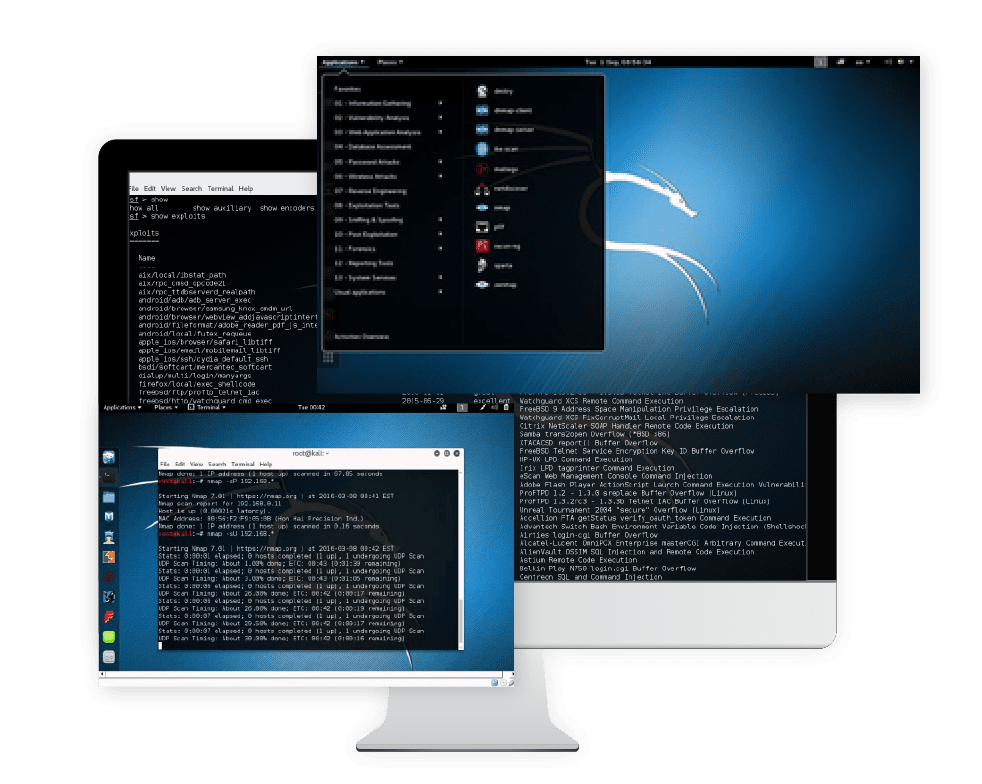
Our external vulnerability assessment will scan for all security flaws on your public facing services that might lead to information leakage or system compromise and we will provide recommended mitigations to help your team plug any issues found.
Internal Penetration Assessment.
Our internal vulnerability assessment is done from the perspective of a malicious individual already in your local network, a usually overlooked part of the network, which we will then look for any issues that could cause information leakage or system compromise. Our report will also include recommendations for mitigating the issues found.
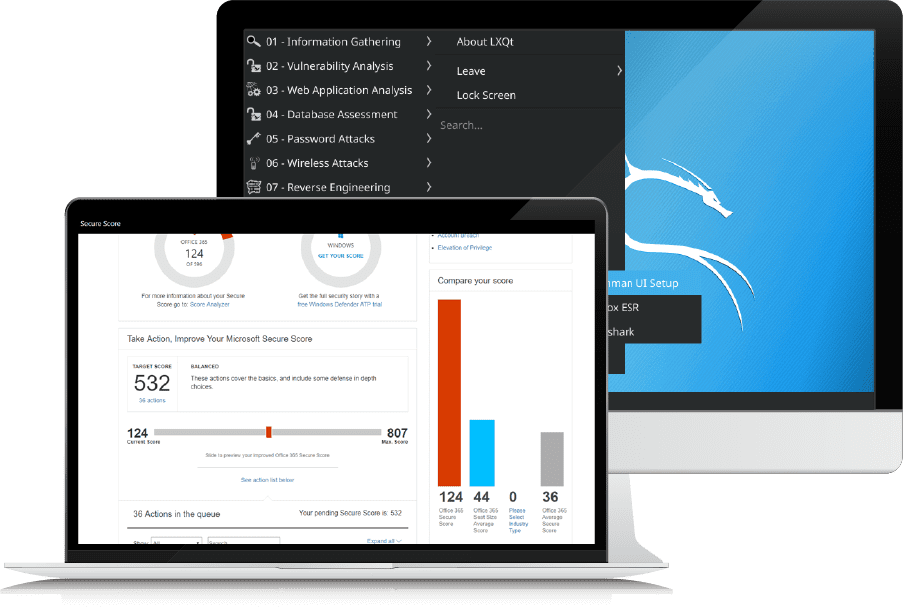
Office 365 Security Assessment.
Understanding cloud security objectives and requirements. Gain an understanding of the customers business requirements and how they drive security objectives and requirements. We also provide guidance, recommendations and best practices on how to successfully implement Office 365 security features and provide a prioritized and actionable Office 365 security road map based on customer security objectives and requirements.
Penetration testing is a great tool for discovering and taking action to mitigate vulnerabilities before the bad guys get to them. Watch this three-minute video highlighting the steps we take when conducting a penetration test.
Testimonials

Randall & Quilter Investment Holdings
The breadth and depth of knowledge within the team is clear and evident and to date GTconsult has helped us on several fronts, Pen testing both internal and external, O365 audits, Secure score, SharePoint, DLP, MDM, BYOD, MFA and Vulnerability scanning to name but a few, which in most cases can result in agreements with several organisation. So to have these services provided and managed all under one roof delivers a far more robust and coordinated approach.
I have only praise for GTconsult during the time we have worked with them and R&Q intend to extend the contract further based on the great partnership that we have established to date.
Adam Shakur,
Chief Information Security Officer

"We enjoy working with GTconsult because they are able to assist us tighten our IT Security Policy and create a security roadmap."
Njabulo Xaba
Mangosuthu University of Technology

..having met with GTconsult and been impressed with their CEO and various service offerings, it was an easy decision to bring them onboard as a trusted partner.
Eugene Van Der Lingen
AHRI

Let us help you enable and secure productivity in your business today.
