What is it?
This issue is largely a Remote Code Execution one, Allowing an attacker with access to the Configuration or Control interface to perform dangerous activities without credentials, or authentication of any form, all with elevated privileges.
In short this allows a 3rd party to take complete control of the device and easily establish a foothold in your corporate network in a matter of minutes. There’s a reason this vulnerability scores a 9.8 on the CVSSv3 scoring.
This is all possible due to a fault in the iControl REST api authentication component effecting the majority of BIG-IP’s software versions from 11.6.1 all the way up to 16.1.2. Thankfully F5 has already released a series of security updates covering various versions of their software which could save you a great deal of troubles. We highly recommend these get patched IMMEDIATELY.
However, It is important to keep in mind that 11.x and 12.x versions of the software will not be patched so workarounds will need to be employed or the software will need to be upgraded to at least 13.x.
Issue Mitigation
Thanks to F5, mitigation of this issue can be as easy as updating to one of the below versions of the software:
17.0.0
16.1.2.2
15.1.5.1
14.1.4.6
13.1.5
3 Temporary Workaround’s exist for when update is not immediately possible. We have provided these below as directly taken from F5’s support article K23605346
“Until it is possible to install a fixed version, you can use the following sections as temporary mitigations. These mitigations restrict access to iControl REST to only trusted networks or devices, thereby limiting the attack surface.
· Block iControl REST access through the self IP address
· Block iControl REST access through the management interface
· Modify the BIG-IP httpd configuration
Block iControl REST access through the self IP address
You can block all access to the iControl REST interface of your BIG-IP system through self IP addresses. To do so, you can change the Port Lockdown setting to Allow None for each self IP address in the system. If you must open any ports, you should use the Allow Custom option, taking care to disallow access to iControl REST. By default, iControl REST listens on TCP port 443 or TCP port 8443 on single NIC BIG-IP VE instances. If you modified the default port, ensure that you disallow access to the alternate port you configured.
Note: Performing this action prevents all access to the Configuration utility and iControl REST using the self IP address. These changes may also impact other services, including breaking high availability (HA) configurations.
Before you make changes to the configuration of your self IP addresses, F5 strongly recommends that you refer to the following articles:
· K17333: Overview of port lockdown behavior (12.x - 16.x)
· K13092: Overview of securing access to the BIG-IP system
· K31003634: The Configuration utility of the Single-NIC BIG-IP Virtual Edition now defaults to TCP port 8443
· K51358480: The single-NIC BIG-IP VE may erroneously revert to the default management httpd port after a configuration reload
If you must expose port 443 on your self IP addresses and want to restrict access to specific IP ranges, you may consider using the packet filtering functionality built into the BIG-IP system. For more information, refer to the following article:
K13383: Configuring CIDR Network Addresses for the BIG-IP packet filter
Block iControl REST access through the management interface
To mitigate this vulnerability for affected F5 products, you should restrict management access only to trusted users and devices over a secure network. For more information about securing access to BIG-IP systems, refer to the following articles:
· K13092: Overview of securing access to the BIG-IP system
· K46122561: Restricting access to the management interface using network firewall rules
· K69354049: Restricting access to the BIG-IP management interface for Configuration Utility and iControl REST services using iptables
Note: Restricting access to the management interface by IP address in httpd is not a viable mitigation for this issue.
Modify the BIG-IP httpd configuration
In addition to blocking access through the self IP addresses and management interface, or as an alternative to blocking access if those options are not possible in your environment, you can modify the BIG-IP httpd configuration to mitigate this issue.
· BIG-IP 14.1.0 and later
· BIG-IP 14.0.0 and earlier
BIG-IP 14.1.0 and later
Impact of procedure: Performing the following procedure should not have a negative impact on your system.
Log in to the TMOS Shell (tmsh) of the BIG-IP system by entering the following command:
tmsh
Open the httpd configuration for editing by entering the following command:
edit /sys httpd all-properties
Locate the line that starts with include none and replace none with the following text:
Note: If the current include statement already contains a configuration other than none, add the following configuration to the end of the current configuration, within the existing double-quotation mark characters (").
"<If \"%{HTTP:connection} =~ /close/i \">
RequestHeader set connection close
</If>
<ElseIf \"%{HTTP:connection} =~ /keep-alive/i \">
RequestHeader set connection keep-alive
</ElseIf>
<Else>
RequestHeader set connection close
</Else>"
After updating the include statement, use the ESC key to exit the editor interactive mode, then save changes by entering the following command:
:wq
At the Save changes (y/n/e) prompt, select y to save the changes.
Save the BIG-IP configuration by entering the following command:
save /sys config
BIG-IP 14.0.0 and earlier
Impact of procedure: Performing the following procedure should not have a negative impact on your system.
Log in to tmsh of the BIG-IP system by entering the following command:
tmsh
Open the httpd configuration for editing by entering the following command:
edit /sys httpd all-properties
Locate the line that starts with include none and replace none with the following text:
Note: If the current include statement already contains a configuration other than none, add the following configuration to the end of the current configuration, within the existing double-quotation mark characters (").
"RequestHeader set connection close"
After updating the include statement, use the ESC key to exit the editor interactive mode, then save changes by entering the following command:
:wq
At the Save changes (y/n/e) prompt, select y to save the changes.
Save the BIG-IP configuration by entering the following command:
save /sys config”
Effected Devices
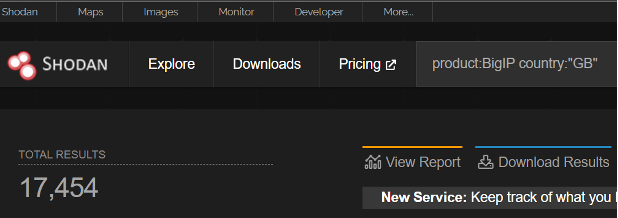
We have taken a look on shodan.io to investigate the scale of this issue and how many devices are potentially at risk just on the public internet and we have the below results separated by area:
In the UK alone we see almost 17,5 thousand potentially at risk devices
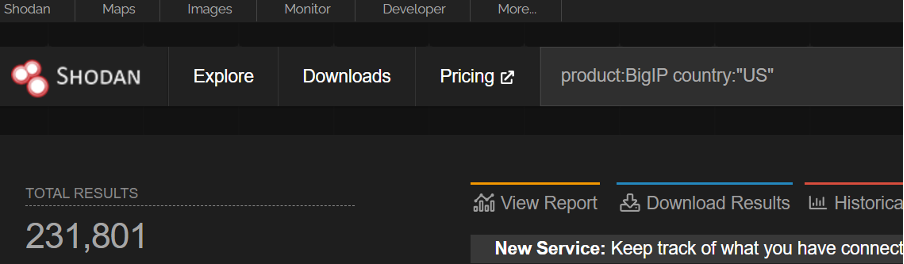
In the United states this number grows to an astounding 231,8 thousand devices
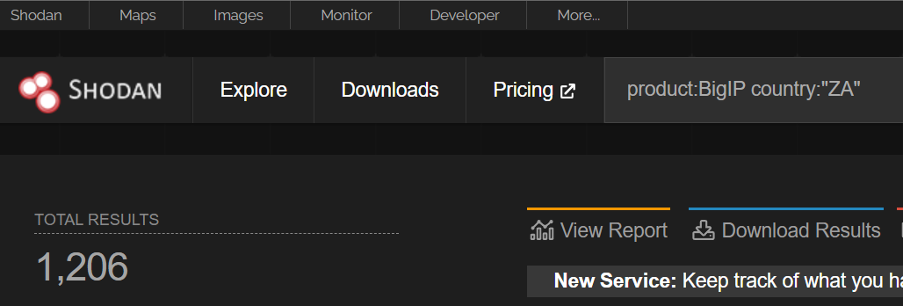
And in our side of the world (South Africa) we can see 1206 devices publicly visible and potentially vulnerable.
A Team Protection offering has already alerted and patched our monitored clients. Find out more on how we can protect you below.
