In a strange stroke of irony, the ransomware group CONTI has had all of their private messages and internal documents leaked
My how the tables have turned. An organization that since 2017 has been infiltrating organizations, dropping ransomware payloads to encrypt and exfiltrate data to later be leveraged for a ransom, has a cool cold slap to the face with a large trout case of karma. CONTI leaks on twitter started dropping files which revealed the internal chats of the organization on February the 27th. Since then, more files have been uploaded, showing the recruitment process of hiring new employees, induction documentation and HOWTO’s on how to hack and deploy the ransomware payloads.
The insight into this organization is no different to any other, they have sales, marketing, administration, payroll and developers.
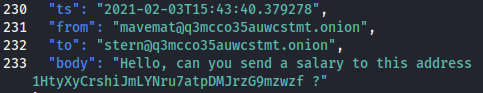
They seem to have normal hours and encourage each other to get sleep if they are working too hard.
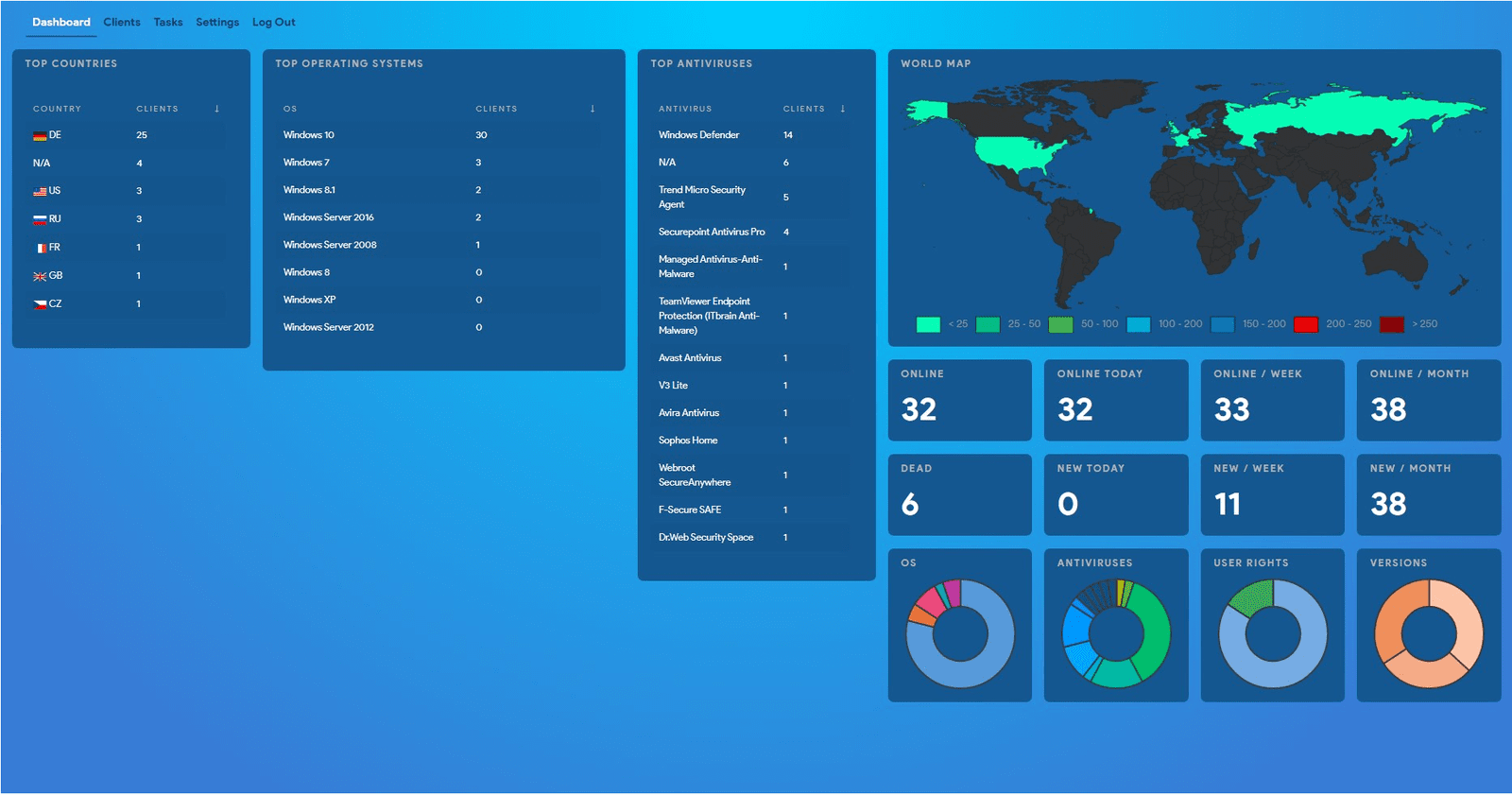
And had pretty good dashboards to show the company's current pipeline, just like we all have. A ransomware CRM if you will.
The truth is they were running one hell of an enterprise, in fact this is what their BTC account looked like.
Yup you read that correctly 65,498 Bitcoins. I made a easy to review graph below based on where you are to understand just how much that is, cause its a lot.
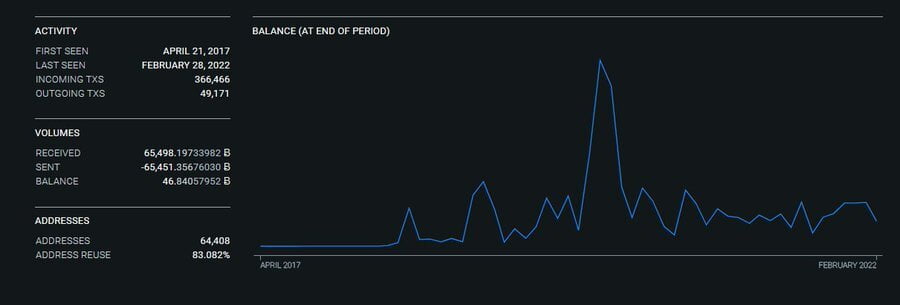
ZAR = R 43 841 065 425
USD = $ 2 848 274 310
GBP = £ 2 124 532 403
I read one of the induction documents labeled “old school spirit” which was translated from the Russian “дух старой школы”. Get the job done culture was created from the very beginning and ensuring that clear simple code was used with only results matter approach.
Look, all of this was to defraud companies from money, and that’s illegal. However, I am still impressed at the speed this organization worked at, their internal training process, and their overall focus on getting things done. It’s why they became the biggest in the world.
How can organizations even think of defending themselves against a super sophisticated team when they themselves don’t even have the most basic processes in place in their own organizations?
The bottom line is if companies are going to defend themselves from ransomware attacks in the future, they are going to have to learn this “Get if done” mentally we see from the CONTI organization. But not on profit and sales, it must be a focus on IT Security and Company culture. Does everyone in the company have MFA enabled with a really strong password that is only used in one place? Do you have security dashboards to show potential threats? Do you have training materials to help educate everyone? Do you have an open chat where people can ask questions and get answers? It's not the be all and end all but it's for sure a great place to get started.

Office 365 Complete Protection
We have categorised all the features and settings in the Admin Center, Secure Score, Security Center, Compliance Centre and Exchange Online Protection into modules that our experienced team can assist your team deploy with a hands on approach .
We ensure that the biggest asset in your company, the people, are educated about the changes, and educated on how to deal with dodgy emails in the future. We protect your backend systems alerting your team to phishy mails, and dodgy looking logins and much more.
