A sophisticated zero-day exploit chain targeting Microsoft SharePoint servers has exploded into a global cybersecurity crisis. Eye Security's research team identified active, large-scale exploitation beginning on July 18, 2025, around 18:00 CET, with attackers compromising dozens of SharePoint servers worldwide within hours SharePoint Under Siege: ToolShell Mass Exploitation. This isn't opportunistic malware—it's surgical exploitation that demonstrates why organizations need dedicated cybersecurity expertise.
The ToolShell Exploit: From Proof-of-Concept to Global Weapon
The ToolShell Exploit: From Proof-of-Concept to Global Weapon
The attack chain, dubbed "ToolShell," weaponizes a combination of CVE-2025-49706 and CVE-2025-49704, originally demonstrated at Pwn2Own Berlin 2025 SharePoint Under Siege: ToolShell Mass Exploitation. What makes this particularly alarming is the speed of weaponization—from academic proof-of-concept to active global exploitation in just 72 hours SharePoint Under Siege: ToolShell Mass Exploitation.
The sophistication of this attack cannot be overstated. Rather than deploying typical web shells, attackers are using stealthy .aspx files designed specifically to extract cryptographic secrets from SharePoint servers, including ValidationKey and DecryptionKey configurations SharePoint Under Siege: ToolShell Mass Exploitation. These stolen keys effectively turn any authenticated SharePoint request into a remote code execution opportunity.
Technical Deep Dive: How the Attack Works
The exploit targets the /_layouts/15/ToolPane.aspx endpoint, allowing attackers to write files to the server without any authentication SharePoint Under Siege: ToolShell Mass Exploitation. The malicious payload extracts the SharePoint server's MachineKey configuration through internal .NET methods, providing attackers with the cryptographic material needed to craft valid __VIEWSTATE payloads.
This mirrors the design weakness from CVE-2021-28474, but now packaged into a modern zero-day chain with automatic shell deployment, full persistence, and zero authentication requirements SharePoint Under Siege: ToolShell Mass Exploitation. The attack essentially turns SharePoint's trust in its own configuration into a weapon.
Global Scale of Compromise
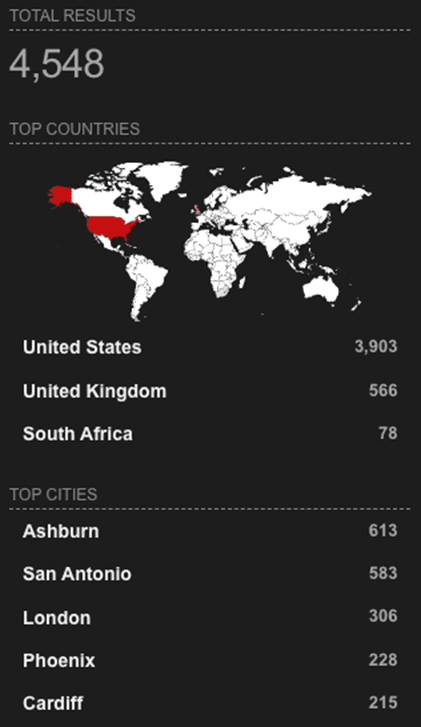
Recent Shodan search data reveals the massive scope of potential targets. With 4,548 total results globally, the geographic distribution shows concerning exposure levels:
Top Countries by Exposure:
These numbers represent just the publicly discoverable SharePoint servers—the actual attack surface is likely much larger when considering internal systems and those behind additional security layers
Active Exploitation Indicators
Eye Security has identified specific indicators of compromise from the active campaign SharePoint Under Siege: ToolShell Mass Exploitation:
Attack Sources:
First wave: 107.191.58.76 (US-based, July 18 around 18:06 CET)
Second wave: 104.238.159.149 (US-based, July 19 around 07:28 CET)
User Agent String:
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Exploit Path:
/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx
GTconsult's Global Response Capability
At GTconsult, our international presence across the UK, USA, and South Africa positions us uniquely to respond to global threats like the ToolShell campaign. Our distributed support teams provide:
24/7 Global Monitoring:
With operations spanning multiple time zones, our security specialists maintain continuous surveillance across all major geographic regions where SharePoint exposure is highest.
Regional Threat Intelligence:
Our teams in London, US operations centers, and South African facilities collaborate to track regional attack patterns and share intelligence about emerging threats.
Rapid Response Coordination:
When zero-day exploits like ToolShell emerge, our global infrastructure enables immediate protective measures across client environments, regardless of geographic location.
Local Compliance Expertise:
Each region brings specialized knowledge of local regulatory requirements and industry standards, ensuring comprehensive protection that meets regional security mandates.
Why This Attack Succeeded—And How We Prevent It
Eye Security's initial detection came through CrowdStrike Falcon EDR deployment, which flagged suspicious process chains on a legacy SharePoint server SharePoint Under Siege: ToolShell Mass Exploitation.
This highlights several critical factors:
Speed of Exploitation: The attack was designed to evade detection and gain long-term access, with exploitation occurring within 72 hours of the public demonstration SharePoint Under Siege: ToolShell Mass Exploitation.
Sophistication of Payload: Unlike typical web shells, the malicious .aspx files were specifically designed to extract cryptographic secrets rather than provide interactive command execution SharePoint Under Siege: ToolShell Mass Exploitation, making detection more challenging.
Scale of Campaign: Eye Security scanned over 1,000 public-facing SharePoint environments and confirmed dozens of compromised servers using the exact same payload SharePoint Under Siege: ToolShell Mass Exploitation.
GTconsult's Proactive Defense Strategy
Our approach to threats like ToolShell demonstrates why reactive security fails in today's threat landscape:
Predictive Threat Modeling:
We maintain comprehensive asset inventories and vulnerability assessments, enabling rapid identification of systems at risk when new exploits emerge.
Advanced EDR Integration:
Like the Eye Security detection that uncovered this campaign, our monitoring solutions include behavioral analysis that can identify zero-day exploitation patterns.
Rapid Patch Management:
Our teams coordinate immediate deployment of security updates across client environments, minimizing exposure windows during critical vulnerability periods.
Compromise Assessment:
When threats emerge, we conduct thorough sweeps to ensure no persistence mechanisms or additional compromises exist.
Immediate Action Items for Organizations
Given the active exploitation of this vulnerability, organizations must act immediately:
Deploy Microsoft's July 2025 Security Update for all SharePoint installations
Scan for Indicators of Compromise in _layouts/15/ directories and HTTP access logs from July 18-19
Rotate Credentials for any systems that may have been exposed
Implement Enhanced Monitoring for SharePoint environments
The Bottom Line
The ToolShell campaign represents a new evolution in cyber threats—sophisticated, rapidly weaponized, and globally coordinated. With Eye Security discovering "dozens of systems actively compromised" in their initial scan SharePoint Under Siege: ToolShell Mass Exploitation, this attack demonstrates that traditional reactive security approaches are insufficient.
Organizations need proactive cybersecurity partners with global reach, advanced threat detection capabilities, and the expertise to respond to zero-day threats within hours, not days. GTconsult's presence across the UK, USA, and South Africa—the regions showing highest SharePoint exposure—positions us to provide exactly this level of protection.
Don't wait for threat actors to target your SharePoint environment. Our support teams are actively monitoring for ToolShell indicators and can immediately assess your organization's exposure. Contact GTconsult today for emergency SharePoint security assessments and ongoing protection against evolving cyber threats.

For immediate assistance with SharePoint compromise assessment or emergency incident response across our UK, USA, and South African operations, contact our global support team at GTconsult.com.
Reference: Shodan search data current as of July 2025, showing global SharePoint server exposure across GTconsult service regions.
